After reading through the article, I had some thoughts:
1. Planning game: Customers decide the scope and timing of releases
=> It is difficult even for PM to perform planning for scope and time. Besides, customers are ambitious so they may try to get the most out of the programmer by setting unrealistic scope and time.
2. On-site customer: A customer sits with the team full-time
=> A assigned customer to the team is currently a staff within a company. This staff must clearly know everything about the requirements so they must be a key staff in the company. It is hard to get them full-time in the project and remove them completely from what they are currently doing.
Bibliography:
Beck, Kent. "Embracing change with extreme programming." Computer 32.10 (1999): 70-77.
Collection of thoughts, notes and other experiences built-up from my studies and researches
Monday, 26 October 2015
[Case] The Scrum proposal
Please refer to the Link for the case made by my lecturer.
After reading the case, I identified some significant points (P):
P1. Most of the engineer's time is for support and maintenance
P2. There is an increasing trend for the support queue activity overtime (Y1 - Y4)
P3. The current project development process is not suitable for existing product maintenance. Management team and engineers propose Agile iterative development lifecycle.
P4. Agile raises an significant concern related to current certified ISO9001.
My recommendations and support arguments include:
For P1 and P2: I don't see the increase in support and maintenance time is an issue because it is an increasing in customer's demands. The demands come with revenue. The company can make money through supporting and maintenance fee. One of my client back in Vietnam did recognize this opportunity and turn it into revenue by divide a product for a customer to a specific team. The team will follow the product to the end (Development to Maintenance). By this way, each team becomes a profit center. In fact, my client reduced the software package and installation fee (one time revenue) to attract more customers and charge more in support and maintenance activities (recurring revenue).
For P3 and P4: Agile is suitable for support and maintenance as well as ISO9001 with the following modifications:
After reading the case, I identified some significant points (P):
P1. Most of the engineer's time is for support and maintenance
P2. There is an increasing trend for the support queue activity overtime (Y1 - Y4)
P3. The current project development process is not suitable for existing product maintenance. Management team and engineers propose Agile iterative development lifecycle.
P4. Agile raises an significant concern related to current certified ISO9001.
My recommendations and support arguments include:
For P1 and P2: I don't see the increase in support and maintenance time is an issue because it is an increasing in customer's demands. The demands come with revenue. The company can make money through supporting and maintenance fee. One of my client back in Vietnam did recognize this opportunity and turn it into revenue by divide a product for a customer to a specific team. The team will follow the product to the end (Development to Maintenance). By this way, each team becomes a profit center. In fact, my client reduced the software package and installation fee (one time revenue) to attract more customers and charge more in support and maintenance activities (recurring revenue).
For P3 and P4: Agile is suitable for support and maintenance as well as ISO9001 with the following modifications:
- Ensure placed controls and documentations throughout the product development and maintenance processes. (ISO9001)
- Product for a specific customer is now allocated to team. Team lead now will become review bugs, customer requests and assign to the next sprint or iteration.
- Pay more attentions on SLA agreement in term of fee, scope for support, time, and quality of the patches.
Tuesday, 20 October 2015
[Research project] Brainstorming some methods for project requirements gathering
Our group [Me and Phuong Tran] wants to understand the "Dublin Bus" Mobile application (App).
Look:
Still-Photo Survey:
How: Follow a planned shooting script and capture pictures of the people using the App
Why: uncover patterns of behavior and perceptions
Fly on the Wall:
How: Observe and record behavior within its context, without interfering with people's activities when they use app.
Why: see what people actually do within real contexts
Learn:
Combine observation with Character Profiles method
How: Based on observations of real people, develop character profiles
Why: Communicate the value to different concepts to various target groups.
Ask:
Extreme User Interviews:
How: individuals who are extremely familiar or completely unfamiliar with the product and ask them to evaluate
Why: highlight key issues
Combine Interviews with Five Whys method
How: Asking "Why?" questions in response to five consecutive answers
Why: force people to examine and express the underlying reasons
Appendices:
Questions for the interview:
Have you ever use Dublin Bus Application on mobile?
If yes,
[Ask them use the App to perform their regular tasks]
Would you mind if I film your activities?
[If yes, Film their activities when they use the App] [If no, observe]
How many times per week do you use it?
Can you tell me something about the App's functions that you prefer? and some that you don't like and want to improve?
[Apply Five Whys method] for each answer.
Have you ever use other similar app for checking bus/train times, locations, buying bus/train tickets?
Are there any function in other apps that you love? Are there any function that you want Dublin Bus app to have?
[Apply Five Whys method] for each answer.
If no,
[Assist the interviewee to use the App]
and perform the above steps
Besides, here are some extra brainstorming ideas for "Try":
Try:
Empathy Tools:
How: tools like clouded glasses + weighted gloves to experiences the processes
Why: prompt an empathic understanding for users with disabilities or special conditions
=> voice commands
Experience Prototype:
How: quickly prototype a concept using available materials and use it to learn from a simulation
Why: reveal unanticipated issues or needs + evaluate ideas
=> build a app prototype
Bibliography:
Ideo Product Development. IDEO Method Cards: 51 Ways to Inspire Design; Learn, Look, Ask, Try. Ideo, 2003.
Look:
Still-Photo Survey:
How: Follow a planned shooting script and capture pictures of the people using the App
Why: uncover patterns of behavior and perceptions
Fly on the Wall:
How: Observe and record behavior within its context, without interfering with people's activities when they use app.
Why: see what people actually do within real contexts
Learn:
Combine observation with Character Profiles method
How: Based on observations of real people, develop character profiles
Why: Communicate the value to different concepts to various target groups.
Ask:
Extreme User Interviews:
How: individuals who are extremely familiar or completely unfamiliar with the product and ask them to evaluate
Why: highlight key issues
Combine Interviews with Five Whys method
How: Asking "Why?" questions in response to five consecutive answers
Why: force people to examine and express the underlying reasons
Appendices:
Questions for the interview:
Have you ever use Dublin Bus Application on mobile?
If yes,
[Ask them use the App to perform their regular tasks]
Would you mind if I film your activities?
[If yes, Film their activities when they use the App] [If no, observe]
How many times per week do you use it?
Can you tell me something about the App's functions that you prefer? and some that you don't like and want to improve?
[Apply Five Whys method] for each answer.
Have you ever use other similar app for checking bus/train times, locations, buying bus/train tickets?
[Apply Five Whys method] for each answer.
If no,
[Assist the interviewee to use the App]
and perform the above steps
Besides, here are some extra brainstorming ideas for "Try":
Try:
Empathy Tools:
How: tools like clouded glasses + weighted gloves to experiences the processes
Why: prompt an empathic understanding for users with disabilities or special conditions
=> voice commands
Experience Prototype:
How: quickly prototype a concept using available materials and use it to learn from a simulation
Why: reveal unanticipated issues or needs + evaluate ideas
=> build a app prototype
Bibliography:
Ideo Product Development. IDEO Method Cards: 51 Ways to Inspire Design; Learn, Look, Ask, Try. Ideo, 2003.
[Study] On the assessment of the strategic value of information technologies: conceptual and analytical approaches
With years of intensive research, no consensus about strategic value of IT reached. This may due to lack of divergent theoretical frameworks applied.
2 predominant conceptual bases are:
- Resource-centered view (IT as a strategic resource that when combined with other strategic resources directly influence org. performance)
- Production function view: Scale of IT resources [size of IT investments]: consider IT capital and labor to be independent production inputs that can affect a broad range of financial measures.
- Resource-based view: Scope of IT resources [nature or uniqueness of IT applications]: resources confer a competitive advantage to a firm only when they are firm-specific, valuable, rare, inimitable, and nonsubstitutable.
=> strategic resource can produce important benefits for firms (reducing costs and improving revenues)
- Contingency-based view (IT business alignment)
- IT resources per se may add little value and play a major role in improving a firm's performance only when they are planned and used to support a firm's main strategic objectives.
- A possible explanation for the inconsistent findings presented could be that different studies have used different approaches to conceptualize SAIT and measure its effect on org. performance.
=> fit: the degree to which the needs, demands, goals, objectives, and/or structure of one component are consistent with the needs, demands, goals, objectives and/or structure of another component. Extent:
- Adaptation (personal - org)
- Compatibility (individual-org)
- Assimilation (org - org)
- Coupling (inter-exter org)
=> focusing on how IT strategy is developed and implemented in conjunction with business strategy => which the IT portfolio of IT applications is aligned with the business objectives of the firm.
The dynamics of unpredictable environments call for a research approach that can fully capture the relationship between bus. strategy, IT strategy and performance.
Components of SAIT:
- Cost-reduction: most efficient producer (minimize operation
- Quality-improvement:
- Revenue-growth:
=> IT alignment with cost reduction strategy generate more immediate and tangible benefits for firms than IT-strategy alignment that aims to facilitate revenue growth.
=> extracting benefits from strategic IS resources designed to help firms grow is more difficult than extracting benefits from operational IS resources developed to cut costs.
Bibliography:
Oh, Wonseok, and Alain Pinsonneault. "On the assessment of the strategic value of information technologies: conceptual and analytical approaches."MIS quarterly (2007): 239-265.
Saturday, 17 October 2015
[Shadow IT Research] Managing Shadow IT Instances–A Method to Control Autonomous IT Solutions in the Business Departments
Following design science research and guided by a multiple-case study, this research aims towards the design and evaluation of a theoretically justified and practically applicable method to manage Shadow IT
The importance of this long-standing phenomenon rises due to
Occurrences of Shadow IT are applications, spreadsheet and database solutions, cloud services, mobile devices, hardware, support structures, or a combination thereof.
Shadow systems, feral systems, grey IT, rogue IT and hidden IT are equivalent keywords
used in literature for Shadow IT
RQ1: What measures are necessary to manage Shadow IT instances?
RQ2: How can organizations define adaptive and efficient IT Governance structures for autonomous IT solutions in the business departments?
Shadow IT characteristics can be viewed similar to those of informal organizational structures
Both, Shadow IT and informal structures, differ from formal rules. They result from peoples’
need to fill gaps in formal structures to cope with tasks. Both phenomena usually emerge spontaneously, driven by employees on the bottom-level.
Therefore, research examines approaches to access, measure, evaluate, and control informal structures, which can be applied to manage Shadow IT
This decision results from two options on how the business side can fulfill an IT need: Either implementing a solution autonomously or formally initiating a demand at the IT department. This option represents a make-or-buy decision. Transaction Cost Theory is used to explain why institutions insource or outsource capabilities.
Step 1: Identify Shadow IT Instances in the Business Processes
Further research on userdriven IT innovations may focus on the promotion of business-located processes, the distribution of innovations into the organization and the hand-over process to the IT department for established solution.
Comments:
Define Shadow IT: applications, spreadsheet and database solutions, cloud services, mobile devices, hardware, support structures, or a combination thereof.
Approach: user-driven
How: Transaction Cost Theory
=> good article to have ideas for future research
Bibliography:
Zimmermann, Stephan, Christopher Rentrop, and Carsten Felden. "Managing Shadow IT Instances–A Method to Control Autonomous IT Solutions in the Business Departments." (2014).
The importance of this long-standing phenomenon rises due to
- increasingly tech-savvy users,
- easy access to web-based solutions,
- and available end user computing tools
Occurrences of Shadow IT are applications, spreadsheet and database solutions, cloud services, mobile devices, hardware, support structures, or a combination thereof.
Shadow systems, feral systems, grey IT, rogue IT and hidden IT are equivalent keywords
used in literature for Shadow IT
RQ1: What measures are necessary to manage Shadow IT instances?
RQ2: How can organizations define adaptive and efficient IT Governance structures for autonomous IT solutions in the business departments?
Shadow IT characteristics can be viewed similar to those of informal organizational structures
Both, Shadow IT and informal structures, differ from formal rules. They result from peoples’
need to fill gaps in formal structures to cope with tasks. Both phenomena usually emerge spontaneously, driven by employees on the bottom-level.
Therefore, research examines approaches to access, measure, evaluate, and control informal structures, which can be applied to manage Shadow IT
This decision results from two options on how the business side can fulfill an IT need: Either implementing a solution autonomously or formally initiating a demand at the IT department. This option represents a make-or-buy decision. Transaction Cost Theory is used to explain why institutions insource or outsource capabilities.
Step 1: Identify Shadow IT Instances in the Business Processes
Step 2: Evaluate the Shadow IT Instances
Step 3: Control the Shadow IT Instances
Comments:
Define Shadow IT: applications, spreadsheet and database solutions, cloud services, mobile devices, hardware, support structures, or a combination thereof.
Approach: user-driven
How: Transaction Cost Theory
=> good article to have ideas for future research
Bibliography:
Zimmermann, Stephan, Christopher Rentrop, and Carsten Felden. "Managing Shadow IT Instances–A Method to Control Autonomous IT Solutions in the Business Departments." (2014).
[Shadow IT Research] Bringing IT out of the shadows
Article's argument:
Shadow IT: describe the use of unauthorised applications within a corporate environment, and the processing or storage of business information on unapproved devices.
So shadow IT is not a new problem.
The terms ‘rogue’ and ‘shadow’ imply illicit behaviour and malicious motives.
However, most instances of shadow IT are driven by convenience.
Using Tools
Comments:
Define Shadow IT: software
Approach: Using Tools to control
How: Using Tools
=> dont like the idea of using tools as its fixed
Bibliography:
Walters, Richard. "Bringing IT out of the shadows." Network Security 2013.4 (2013): 5-11.
Shadow IT: describe the use of unauthorised applications within a corporate environment, and the processing or storage of business information on unapproved devices.
So shadow IT is not a new problem.
The terms ‘rogue’ and ‘shadow’ imply illicit behaviour and malicious motives.
However, most instances of shadow IT are driven by convenience.
Using Tools
Comments:
Define Shadow IT: software
Approach: Using Tools to control
How: Using Tools
=> dont like the idea of using tools as its fixed
Bibliography:
Walters, Richard. "Bringing IT out of the shadows." Network Security 2013.4 (2013): 5-11.
[Shadow IT Research] Shadow IT A view from behind the curtain
1. What type of Shadow IT software is used in organisations?
2. What are the IT risks for organisational information security when using Shadow IT software?
3. Does the IT risk increase when using open-source Shadow IT software? (Yes)
4. What is the motivation to use Shadow IT?
The study used triangulation approach [The idea is that one can be more confident with a result if different methods lead to the same result] to investigate the Shadow IT phenomena and its findings open Pandora's Box as they lay a new picture of what Shadow IT looks like from the software perspective
Risk bring by Shadow IT: Information Security (Most significant), Compliance issues, wasted time, inconsistent business logic, increased risks for data loss or leaks, wasted investment, etc.,
Research Methods:
Findings:
The report argues that employees are much more tech savvy than they were a decade ago. This fact also means that employees will have no issue bypassing IT departments. => educate them better on [the] risks that their acts may have’ => raising awareness not providing policies that noone reads
1. What type of Shadow IT software is used in organisations?
1) productivity software (e.g. Google apps),
2) communication software (e.g. Skype),
3) utility tools (e.g. CCleaner or 7-Zip),
4) internet browsers (e.g. Firefox), and
5) PDF tools (e.g. PDFCreator)
6. Greynet: Network applications installed by the end users that use evasive techniques to traverse the network.
4. What is the motivation to use Shadow IT?
employees extensively use Shadow IT software that leverages their productivity and enables faster
and better collaboration and communication. Moreover, employees believe that they are not doing anything wrong and simple naivete is driving their behaviours
Restriction is a valid countermeasure, but not a solution, to Shadow IT challenges that can become
opportunities for the entire organisational ecosystem
Comments:
Define Shadow IT: software, hardware, other solution
Approach: user-driven
How: not mentioned
=> good article to have some background understanding of Shadow IT
Bibliography:
Silic, Mario, and Andrea Back. "Shadow IT–A view from behind the curtain." Computers & Security 45 (2014): 274-283.
2. What are the IT risks for organisational information security when using Shadow IT software?
3. Does the IT risk increase when using open-source Shadow IT software? (Yes)
4. What is the motivation to use Shadow IT?
The study used triangulation approach [The idea is that one can be more confident with a result if different methods lead to the same result] to investigate the Shadow IT phenomena and its findings open Pandora's Box as they lay a new picture of what Shadow IT looks like from the software perspective
Risk bring by Shadow IT: Information Security (Most significant), Compliance issues, wasted time, inconsistent business logic, increased risks for data loss or leaks, wasted investment, etc.,
- 1. in-depth analysis of organisational Shadow IT software. Fortune 500 firm that has over 10,000 employees. data collected from the firm's endpoints where each endpoint (PC, laptop, etc.) was scanned and all installed software was retrieved
- 2. four practitioner surveys found online.
- 3. Case study
- 4. Literature review
Findings:
The report argues that employees are much more tech savvy than they were a decade ago. This fact also means that employees will have no issue bypassing IT departments. => educate them better on [the] risks that their acts may have’ => raising awareness not providing policies that noone reads
- 1) Risks behind Shadow IT use are high;
- 2) Data integrity and account information represent the biggest threats;
- 3) Employees are aware of the possible risks when using Shadow IT;
- 4) IT policies are either non-existent or unclear to employees; and
- 5) Employees, despite their knowledge about the risk, continue their behaviours.
1. What type of Shadow IT software is used in organisations?
1) productivity software (e.g. Google apps),
2) communication software (e.g. Skype),
3) utility tools (e.g. CCleaner or 7-Zip),
4) internet browsers (e.g. Firefox), and
5) PDF tools (e.g. PDFCreator)
6. Greynet: Network applications installed by the end users that use evasive techniques to traverse the network.
4. What is the motivation to use Shadow IT?
employees extensively use Shadow IT software that leverages their productivity and enables faster
and better collaboration and communication. Moreover, employees believe that they are not doing anything wrong and simple naivete is driving their behaviours
Restriction is a valid countermeasure, but not a solution, to Shadow IT challenges that can become
opportunities for the entire organisational ecosystem
Comments:
Define Shadow IT: software, hardware, other solution
Approach: user-driven
How: not mentioned
=> good article to have some background understanding of Shadow IT
Bibliography:
Silic, Mario, and Andrea Back. "Shadow IT–A view from behind the curtain." Computers & Security 45 (2014): 274-283.
Friday, 16 October 2015
[Shadow IT Research] Shadow IT Is Out of the Closet
Article's Argument:
Cloud is one of the reason for the rise of Shadow IT
Line of business are now getting their own official technology budgets for non-standard software products. Shadow IT has been freshly-labeled "departmental IT"
IT department is busy with maintaining operating systems and reacting to the demand of increasingly tech-savvy user community.
Talk about the idea of small, controlled projects is more efficient.
Apply structured taxonomy to propose IT initiatives based quantifiable metrics like complexity, breadth of need and ROI.
IT can transform itself from "we build everything" to "here's how to build it", and thus be viewed as a competency center focused not on technology, but on process creation and refinement. IT delivering straightforward development methodologies to business departments, coaching them on how to build their own systems, streamlines deployment, ensures domain expertise, eases organizational tensions, and drives economies of scale.
Comments
Define Shadow IT: software,
Approach: user-driven
How: focus on process, development methodologies for business departments, coaching
=> good article with ideas of new development methodologies, coaching
Bibliography:
Dyché, Jill. "Shadow IT Is Out of the Closet." Harvard Business Review (2012).
Cloud is one of the reason for the rise of Shadow IT
Line of business are now getting their own official technology budgets for non-standard software products. Shadow IT has been freshly-labeled "departmental IT"
IT department is busy with maintaining operating systems and reacting to the demand of increasingly tech-savvy user community.
Talk about the idea of small, controlled projects is more efficient.
Apply structured taxonomy to propose IT initiatives based quantifiable metrics like complexity, breadth of need and ROI.
IT can transform itself from "we build everything" to "here's how to build it", and thus be viewed as a competency center focused not on technology, but on process creation and refinement. IT delivering straightforward development methodologies to business departments, coaching them on how to build their own systems, streamlines deployment, ensures domain expertise, eases organizational tensions, and drives economies of scale.
Comments
Define Shadow IT: software,
Approach: user-driven
How: focus on process, development methodologies for business departments, coaching
=> good article with ideas of new development methodologies, coaching
Bibliography:
Dyché, Jill. "Shadow IT Is Out of the Closet." Harvard Business Review (2012).
[Shadow IT Research] Shadow IT Evaluation Model
Shadow IT: supplement of "official" IT by several, autonomous developed IT systems, processes and organizational units
Different from EUC (End user computing) - which is initiated and supported by IT department.
Young employees with a strong bond to the usage of IT
Increasing focus on compliance and risk management
=> integrated methodology to handle shadow IT
=> IT asset portfolio (map the technical quality and the business value of IS) could be used as a starting point. I set of criterias are given:
=> Assess the risk and opportunities of shadow IT have been regards
=> the evaluation model criterias can be develop further into "User-Driven IT"
Comments:
Define Shadow IT: software, hardware, services, processes organizational units
Approach: user-driven
How: provide a evaluation criterias, meeting between IT and Business for discussion
=> good article with ideas of discussion between IT and Business
Bibliography:
Rentrop, Christopher, and Stephan Zimmermann. "Shadow IT evaluation model." Computer Science and Information Systems (FedCSIS), 2012 Federated Conference on. IEEE, 2012.
Different from EUC (End user computing) - which is initiated and supported by IT department.
Young employees with a strong bond to the usage of IT
Increasing focus on compliance and risk management
=> integrated methodology to handle shadow IT
=> IT asset portfolio (map the technical quality and the business value of IS) could be used as a starting point. I set of criterias are given:
- A. Relevant
- B. Quality
- C. Size
- Initiative potential
- Parallelism
=> the criterias must be discussed between IT and Business
=> Assess the risk and opportunities of shadow IT have been regards
=> the evaluation model criterias can be develop further into "User-Driven IT"
Comments:
Define Shadow IT: software, hardware, services, processes organizational units
Approach: user-driven
How: provide a evaluation criterias, meeting between IT and Business for discussion
=> good article with ideas of discussion between IT and Business
Bibliography:
Rentrop, Christopher, and Stephan Zimmermann. "Shadow IT evaluation model." Computer Science and Information Systems (FedCSIS), 2012 Federated Conference on. IEEE, 2012.
[Shadow IT Research] Management Matters: Shadow IT
Article's arguments:
User want to use the latest application, wireless technologies
The problem with shadow IT poses security risks
Fighting Shadow IT could be counterproductive. => Agencies that institute prohibitive policies will face substantial pushback. (IT controls)
Find the right balance between individual productivity and the needs of the IT department
=> Just highlighting the stuff you cannot do is a bad way
=> create "white lists" of approved applications and popular web destinations
Comments:
Define Shadow IT: software, hardware, services
Approach: IT controls
How: create checklists for what can do, what cannot
=> cannot create the huge checklist like that
Bibliography:
Noyes, Andrew. "Management Matters: Shadow IT."Government Executive 10 (2007).
User want to use the latest application, wireless technologies
The problem with shadow IT poses security risks
Fighting Shadow IT could be counterproductive. => Agencies that institute prohibitive policies will face substantial pushback. (IT controls)
Find the right balance between individual productivity and the needs of the IT department
=> Just highlighting the stuff you cannot do is a bad way
=> create "white lists" of approved applications and popular web destinations
Comments:
Define Shadow IT: software, hardware, services
Approach: IT controls
How: create checklists for what can do, what cannot
=> cannot create the huge checklist like that
Bibliography:
Noyes, Andrew. "Management Matters: Shadow IT."Government Executive 10 (2007).
[Shadow IT Research] The Upside of Shadow IT
Article's arguments:
Employees have been doing an end run around corporate IT using shadow IT systems
Systems built and used in companies without organizational approval
IT controls less than 50% of corporate technology expenditures
CIO are embracing and even encouraging so-called rogue IT.
IT focuses on what data the application use, whether or not an application is mission-critical, and who is in the best position to know the application is running properly.
=> forcus on managing risk
IT getting ahead of technologies, users will now come to us when they want to use something like Basecamp, when they do, we tell them about Central Desktop, similar cloud-based project management service but with better integration into the enterprise.
=> save money, IT as an initiative
Redefine IT's Role as Educator and Policymaker
Sales and marketing department (front-line workers)
Comments:
Define Shadow IT: systems type
Approach: user-driven
How: manage risks, educate users
=> good article with ideas
Bibliography:
King, Julia. "The upside of shadow IT."Computerworld 46.8 (2012): 18-23.
Employees have been doing an end run around corporate IT using shadow IT systems
Systems built and used in companies without organizational approval
IT controls less than 50% of corporate technology expenditures
CIO are embracing and even encouraging so-called rogue IT.
IT focuses on what data the application use, whether or not an application is mission-critical, and who is in the best position to know the application is running properly.
=> forcus on managing risk
IT getting ahead of technologies, users will now come to us when they want to use something like Basecamp, when they do, we tell them about Central Desktop, similar cloud-based project management service but with better integration into the enterprise.
=> save money, IT as an initiative
Redefine IT's Role as Educator and Policymaker
Sales and marketing department (front-line workers)
Comments:
Define Shadow IT: systems type
Approach: user-driven
How: manage risks, educate users
=> good article with ideas
Bibliography:
King, Julia. "The upside of shadow IT."Computerworld 46.8 (2012): 18-23.
[Shadow IT Research] Bringing IT out of the shadows
Author's arguments:
Shadow IT – where business users implement a solution outside the official corporate architecture
without consulting the IT department – can include everything from the use of free online services to departmental decisions to adopt SaaS solutions, let alone the actual importing of users’ own hardware devices.
After all, the prime driver for shadow IT is the desire to do one’s job effectively and to use whatever
tools can help – so an IT department that forbids this is no-one’s friend.
Policy-based networking offers a very useful solution to this dilemma.
The IT Department is now relieved of the need to play the heavy-handed policing role
Comments:
Define Shadow IT: software, services, harware
Approach: IT controls
How: make policies, control networks
Policy is only a way of restricting users. => IT department that forbids this is no-one’s friend
Bibligography:
Johnson, Steve. "Bringing IT out of the shadows." Network Security 2013.12 (2013): 5-6.
Shadow IT – where business users implement a solution outside the official corporate architecture
without consulting the IT department – can include everything from the use of free online services to departmental decisions to adopt SaaS solutions, let alone the actual importing of users’ own hardware devices.
After all, the prime driver for shadow IT is the desire to do one’s job effectively and to use whatever
tools can help – so an IT department that forbids this is no-one’s friend.
Policy-based networking offers a very useful solution to this dilemma.
The IT Department is now relieved of the need to play the heavy-handed policing role
Comments:
Define Shadow IT: software, services, harware
Approach: IT controls
How: make policies, control networks
Policy is only a way of restricting users. => IT department that forbids this is no-one’s friend
Bibligography:
Johnson, Steve. "Bringing IT out of the shadows." Network Security 2013.12 (2013): 5-6.
[Shadow IT Research] Exploring the Shadows: IT Governance Approaches to User-Driven Innovation
Article's arguments: What approaches to SIT are available in literature and are implemented by practitioners?
Napa Country government had begun infiltrating their business environment with their personal mobile devices insisting on using them instead of the provided infrastructure = > how the roles of users and IT are changing in today’s world of ubiquitous computing
Shadow IT Solutions (SIT) pose a major financial, legal and reputational threat to organisations
as they are not verified to comply with any of the organisation’s information security or architectural
policies
Other proposed research question:
1. What ISsec measures are suggested and applied to mitigate the risk of well-intended user-non compliance (user-driven IT solutions)?
2. What are the key factors that cause Business-IT-misalignment and encourage user-driven IT solutions?
3. What ITG mechanisms are suggested and applied to identify and harness the potential of user-driven IT solutions?
Bibliography:
Györy, Andreas, et al. "Exploring the Shadows: IT Governance Approaches to User-Driven Innovation."ECIS. 2012.
Napa Country government had begun infiltrating their business environment with their personal mobile devices insisting on using them instead of the provided infrastructure = > how the roles of users and IT are changing in today’s world of ubiquitous computing
Shadow IT Solutions (SIT) pose a major financial, legal and reputational threat to organisations
as they are not verified to comply with any of the organisation’s information security or architectural
policies
Other proposed research question:
1. What ISsec measures are suggested and applied to mitigate the risk of well-intended user-non compliance (user-driven IT solutions)?
2. What are the key factors that cause Business-IT-misalignment and encourage user-driven IT solutions?
3. What ITG mechanisms are suggested and applied to identify and harness the potential of user-driven IT solutions?
Non-compliance of users with ISsec policies, often referred to as “insider threat”, is identified as one of the top ISsec threats in organisations. Therefore non-compliant user-driven innovations – SIT –
pose a security threat in organizations.
We chose to address situations where SIT is implemented intentionally to support a business
process (low-grade) and not to maliciously inflict (high-grade) economic damage.
Behrens (2009) suggests that SIT solutions operate in the fringes of organisations filling a gap between the requirements of the users and the solutions provided by the IT department.
Poor BITA is caused by either the lack of IT capabilities or the lack of adaptability of business processes or the involved employees. Both cases encourage the development of SIT.
As user-driven IT innovations are an indicator for poor alignment and at the same time offer an operational solution, SIT may offer multiple opportunities for ITG practitioners to improve alignment.
Reasons for short-term misalignment are the detachment of IT and business employees:
- Lack of communication
- Decreased responsiveness invisibility of the IT staff
- Missing shared knowledge
Decentralised IT units have the ability to cater closer to the user needs while a centralised unit has greater potential to achieve economies of scope
Communication has the highest importance. Our IT coordinators are our eyes and ears in every business unit, so we can respond to new business needs quickly.
To achieve this, organisations “have a dedicated budget to integrate user-driven solutions (scripts), which become business-critical”
Empowered users to secure
their own working environment and focuses on protecting the centralised infrastructure and services
according to web standards =>
empowerment requires high user IT skills and an aware
and responsible mind-set and high security set-up costs for infrastructure and services
=>
this may only be feasible for small organisations
The user-oriented approach combines the advantages of the IT-control and the user-driven approach by applying them differently throughout their portfolio: “While transparency is my highest priority, I do believe that a healthy extent of SIT is essential to offer flexibility and space for new ideas and innovation.
We conclude that the user-oriented approach can be adapted to balance efficient operation and the effective use of IT through user-driven innovation within defined boundaries. However the level of freedom differs within the interviewed organizations. To apply this approach a thorough risk assessment (Benaroch et al., 2006) is suggested beforehand to define the boundaries of user innovation.
The most common cited risks were:
- Data security and compliance,
- efficiency and synergy losses,
- lacking continuity and the disruption of a controlled environment.
Practitioner approach to SIT is depending on their strategic orientation. Approaches can be divided into three groups:
- IT-control
- User-orientated
- and user-driven.
Comments:
=> Research question can be: How to use Shadow IT as multiple opportunities for ITG practitioners to improve ITB alignment in large companies?
=> How can small size business approach Shadow IT as an source of innovation at small size business?
=> How to make Shadow IT as an valuable input for Organizational/IT strategy?
=> How to recognize user-driven IT innovations using Shadow IT?
=> How to make Shadow IT as an valuable input for Organizational/IT strategy?
=> How to recognize user-driven IT innovations using Shadow IT?
Györy, Andreas, et al. "Exploring the Shadows: IT Governance Approaches to User-Driven Innovation."ECIS. 2012.
[Shadow IT Research] The future of enterprise IT in the cloud
Article's arguments:
Increasing in adoption of cloud services demands new methodologies, tools and skill sets for managing hybrid portfolio (services + traditional IT systems)
3 Trends are mentioned:
Consumer-driven IT services:
IT service provider explosion:
My comments:
Bibliography:
Erbes, Jamie, Hamid R. Motahari-Nezhad, and Sven Graupner. "The future of enterprise IT in the cloud." computer 5 (2012): 66-72.
Sykes, R. "The CIO Is Dead. Long Live the Master Operational Strategist." CIO Magazine 2 (2010).
Increasing in adoption of cloud services demands new methodologies, tools and skill sets for managing hybrid portfolio (services + traditional IT systems)
3 Trends are mentioned:
- Trend 1: Cloud services: change roles from providing IT systems to managing services;
- Trend 2: IT Consumerization: BYOD to accessing services;
- Trend 3: Increasing cross-enterprise collaboration: sharing, exchanging and managing information across enterprise IT walls.
Consumer-driven IT services:
- IT departments should concentrate on how to enable and allow these consumer devices to connect safely and manageably to enterprise networks
IT service provider explosion:
- Individual business units and employees make decisions about external IT service consumption
- IT cannot manage centrally [Finance], [Security], [Responsibility], [Compliance]
Managing a hybrid IT ecosystem:
- Understand the types of services consuming or might need in near term
- Beware of various ways to obtain them for the enterprise in the future
- Trend to CIO's role away from managing IT "build and operate" functions to manage people, processes and technologies
Shifting basic for value:
- Traditionally: centralized roles: consolidation, centralization and standardization
- Shadow IT > Shadow Sourcing
- New: contracting, integrating and managing relationships with service providers
Managing a hybrid portfolio
- Require new mechanisms and frameworks that support the end-to-end life cycle of services throughout acquisition, integration, consumption, financial management, and termination
- Concept of service portfolio management
- adapted part of the Information Technology Infrastructure Library (ITIL) methodology
My comments:
=> cannot solve the problem of time for usage readiness and bus users wants to use it immediately, don't like the idea of standard framework cause framework cannot use for all situations in different companies.
Bibliography:
Erbes, Jamie, Hamid R. Motahari-Nezhad, and Sven Graupner. "The future of enterprise IT in the cloud." computer 5 (2012): 66-72.
Sykes, R. "The CIO Is Dead. Long Live the Master Operational Strategist." CIO Magazine 2 (2010).
Tuesday, 13 October 2015
[Study] Sample of User requirements
Please find the sample in the link:
https://www.google.ie/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&cad=rja&uact=8&ved=0CB8QFjAAahUKEwiY_6eenb_IAhUE2hoKHZbnB6U&url=http%3A%2F%2Fwww.mesh-ip.eu%2Fupload%2Fmesh-wp6-D6.3-20061116-User%2520Requirements-v4b.pdf&usg=AFQjCNFOaWxMjrwgIQGTUJ9bLG_wN0K_IQ&sig2=zkOpodsXyu2SYyPKZWdMpQ&bvm=bv.104819420,d.d24
The contents include:
https://www.google.ie/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&cad=rja&uact=8&ved=0CB8QFjAAahUKEwiY_6eenb_IAhUE2hoKHZbnB6U&url=http%3A%2F%2Fwww.mesh-ip.eu%2Fupload%2Fmesh-wp6-D6.3-20061116-User%2520Requirements-v4b.pdf&usg=AFQjCNFOaWxMjrwgIQGTUJ9bLG_wN0K_IQ&sig2=zkOpodsXyu2SYyPKZWdMpQ&bvm=bv.104819420,d.d24
The contents include:
- The methodology for gathering requirements: Focus Group, Questionnaires, ...
- Requirements are formatted using Use Cases, Functional and Non-Functional Requirements (what the system should do vs how the system works)
[Case] IONA 2
First Time: Quick skimming
Second Time: Things that I don't know:
ORB (Object Request Broker): The Object Request Broker (ORB) is middleware that uses the CORBA specification. The Object Request Broker or ORB takes care of all of the details involved in routing a request from client to object, and routing the response to its destination.
BEA Systems: was a company specialized in enterprise infrastructure software products which was wholly acquired by Oracle Corporation on April 29, 2008
Kent Beck: Test Driven Development: By Example is a book about a software development technique by Kent Beck. Beck's concept of test-driven development centers on two basic rules:
Third Time: Organizational Aspects:
Culture:
Small nimble close knit teams, everyone knew everyone and no one let formality get in the way of celebrating success or getting to the heart of a problem.As a place to work it was hectic, razor sharp, direct and fun.
But the business model wasn’t Iona; Iona was the people.
Problems:
https://en.wikipedia.org/wiki/Middleware
http://www.service-architecture.com/articles/web-services/corba.html
https://en.wikipedia.org/wiki/BEA_Systems
https://en.wikipedia.org/wiki/Test-Driven_Development_by_Example
https://www.quora.com/What-is-the-difference-between-C-C++-and-C
Second Time: Things that I don't know:
ORB (Object Request Broker): The Object Request Broker (ORB) is middleware that uses the CORBA specification. The Object Request Broker or ORB takes care of all of the details involved in routing a request from client to object, and routing the response to its destination.
Middleware is computer software that provides services to software applications beyond those available from the operating system.
CORBA is the acronym for Common Object Request Broker Architecture. It was developed under the auspices of the Object Management Group (OMG). It is middleware. A CORBA-based program from any vendor, on almost any computer, operating system, programming language, and network, can interoperate with a CORBA-based program from the same or another vendor, on almost any other computer, operating system, programming language, and network.
The first service-oriented architecture for many people in the past was with the use of Object Request Brokers (ORBs) based on the CORBA specification. The CORBA specification is responsible for really increasing the awareness of service-oriented architectures.
ART (Adaptive Runtime Technology): ORB? distributed computing engine? replace Orbix?BEA Systems: was a company specialized in enterprise infrastructure software products which was wholly acquired by Oracle Corporation on April 29, 2008
- Tuxedo - transaction-oriented middleware platform
- BEA Weblogic, now Oracle Weblogic Server - Java EE enterprise infrastructure platform
- AquaLogic, now Oracle Service Bus - Service-Oriented Architecture (SOA) platform
Kent Beck: Test Driven Development: By Example is a book about a software development technique by Kent Beck. Beck's concept of test-driven development centers on two basic rules:
- Never write a single line of code unless you have a failing automated test.
- Eliminate duplication.
- The book illustrates the use of unit testing as part of the methodology, inclu
- ding examples in Java and Python. One section includes using test-driven development to develop a unit testing framework.
Third Time: Organizational Aspects:
Culture:
Small nimble close knit teams, everyone knew everyone and no one let formality get in the way of celebrating success or getting to the heart of a problem.As a place to work it was hectic, razor sharp, direct and fun.
But the business model wasn’t Iona; Iona was the people.
Problems:
- Lack of HR due to R&D was dragged down by Customer Support, there was no solution yet.
- Cost: building
- Culture changing: community lost
- Begins to use management system approach (ITIL...) => best practice with Kent Beck
- Communication problem dues to rise of people in team
- Cost for supporting legacy customer increases
- New technologies (XML based app servers) => new generation tech (ART)
References:
http://managingdesignanddevelopment.blogspot.ie/2012/10/iona-2-case.html
http://www.service-architecture.com/articles/web-services/object_request_broker_orb.html
https://en.wikipedia.org/wiki/Middleware
http://www.service-architecture.com/articles/web-services/corba.html
https://en.wikipedia.org/wiki/BEA_Systems
https://en.wikipedia.org/wiki/Test-Driven_Development_by_Example
https://www.quora.com/What-is-the-difference-between-C-C++-and-C
Monday, 12 October 2015
[Study] A field study of the software design process for large systems
A layered behavioral model of software development processes:
Reference
Curtis, B, Krasner, H and Iscoe, N, 1999. A field study of the software design process for large systems. Communications of the ACM, 31 (11), pp.1268-1287.
- Researches have demonstrated the substantial impact of behavioral factors on software productivity. The effects of tools and methods were relatively small in these studies.
- Software design is often described as a problem-solving activity.
- Since large software systems are still generated by humans rather than machines, their creation must be analyzed as a behavioral process. In fact, software development should be studied at several behavioral leveis
Reference
Curtis, B, Krasner, H and Iscoe, N, 1999. A field study of the software design process for large systems. Communications of the ACM, 31 (11), pp.1268-1287.
[Study] The fiction of methodological development: a field study of information systems development
How systems analysts design IS in practice and how methodologies are used in this process?
This article describes the findings of a field study of the IS development process in a large organization.
Methodologies may also be developed by combining different types of methodologies to overcome the drawbacks of each.
Research approach:
This is an ``ecological'' approach to IS development research as advocated by Shneiderman and Carroll (1988). It involves the collection of detailed, qualitative data on development practice in specific contexts. Ethnography involves deep immersion in the research context over an extended period of time.
- At the start of the study, data were collected using the participant observation approach.
- This was then followed by unstructured interviews of the key players of the EIS team.
- These field notes were then transcribed into a rich case study describing the EIS development process and important aspects of the real-life context.
- During the analysis, the case study and field notes were read several times, and coded systematically to identify key issues and concepts.
- These initial issues and concepts were analysed and aggregated to articulate a set of common or recurring themes.
The use of methodologies for IS development
IS development in practice is not a sequential process
Discussion: implications for IS development methodologies
The above analysis indicates that the process of EIS development at LMC appeared to be characterized by improvisation, opportunism, interruption and mutual negotiation as much as by progress milestones, planning and management control.
The more team members ignored or overrode the methodology during their design practice, the better they were able to exploit opportunities and changing situations by applying professional judgement and knowledge
Development work regularly requires ad hoc problem-solving skills and abilities such as creativity which cannot be easily pre-planned.
The evidence suggests that social controls, such as norms promoting collaboration with colleagues, professional design practices and established routines appeared to be a more significant influence on developers' work practice at LMC than the requirements of a methodology. Training and appraisal programmes might potentially play a more significant part in producing and reinforcing such control
Reference:
Nandhakumar, J and Avison, D, 1999. The fiction of methodological development: a field study of information systems development: a field study of information systems development. Information Technology & People, 12 (2), pp.176 - 191.
[Study] The chaos model and the chaos cycle
Focus on the role of the developer, the author used the chaos principles as a metaphor to connect the gap between one line of code and the entire project understanding.
The Chaos Model
A combination between linear problem solving loop with fractals used to describe the complexity of software development.
The model imposes little organization on the development process to allow organizations to evolve and therefore can be applied in many complex situations.
Reductionist approach is used to deal with large problems. Fractals require subproblems of any one problem have approximately the same size and value.
The Linear Problem-Solving Loop
4 stages include: Status quo, problem definition, technical development and solution integration.
The loop begins and ends with a status quo.
4. The status quo:
Reference:
Raccoon, L. B. S., 1995. he chaos model and the chaos cycle. ACM SIGSOFT Software Engineering Notes, 20 (1), 55-66.
The Chaos Model
A combination between linear problem solving loop with fractals used to describe the complexity of software development.
The model imposes little organization on the development process to allow organizations to evolve and therefore can be applied in many complex situations.
Reductionist approach is used to deal with large problems. Fractals require subproblems of any one problem have approximately the same size and value.
The Linear Problem-Solving Loop
4 stages include: Status quo, problem definition, technical development and solution integration.
The loop begins and ends with a status quo.
1. Problem definition:
- Choose problem to solve
- Define solution's constraints
- Solving problem may or may not be possible
2. Technical Development:
- Do the work
- Developers may or may not ensure that the right problem gets solved
3. During Solution integration:
- Integrate technical solving results to the world at large
- Communicate to users
- Users may rejects or ignore b/c they may find it wrong
4. The status quo:
- Represent the current state of affairs in the world
- As the new technical solution gains acceptance, a new status quo emerges and the cycle repeats.
The fractal Problem-Solving Loop
The Linear Problem-Solving Loop applies in many project levels
- Entire project
- Sub-group
- Individual developer
Example for project levels:
An integration of the chaos model:
User's needs
Technical Resources
Developers solve mid-level problems
Fractal phase definitions
Reference:
Raccoon, L. B. S., 1995. he chaos model and the chaos cycle. ACM SIGSOFT Software Engineering Notes, 20 (1), 55-66.
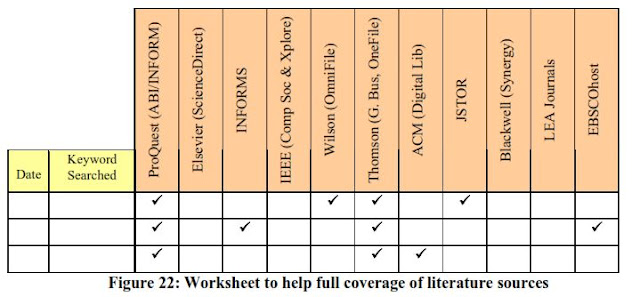
[Study] A systems approach to conduct an effective literature review in support of information systems research
Levy and Ellis (2006) stated the following:
A. OVERALL
What is a Research:
a. Research must enhance the current understanding of a phenomenon, or contribute to enhance the BoK
What is a Literature Review:
- a) methodologically analyze and synthesize quality literature,
- b) provide a firm foundation to a research topic,
- c) provide a firm foundation to the selection of research methodology, and
- d) demonstrate that the proposed research contributes something new to the overall body of knowledge or advances the research field’s knowledge-base. [uncovers areas where research is needed]
- Quality literature stimulates additional research studies, thus providing validation of the original theory proposed
- The selection of the methodology should not be interpreted as placing more rigor on one type of research but enable them to provide justifications for why a given approach is optimal for their study.
- The keyword search should be just the initial, not the main step for a literature search.
- A common mistake by novice researchers, specifically in IS, is to assume that the keyword search yields all that is available from the literature:
- keywords of IS literature tend to have a limited life span (MRP in 1970s, ERP in 1990s)
- use of technology specific terms or ‘buzzwords’that appear and disappear from literature
- Step 1: backward references search
- reviewing the references of the articles yielded from the keyword search noted above
- Doing so will enable the researcher to extend his or her knowledge even deeper on the phenomenon under study
- Step 2: backward authors search
- reviewing what the authors have published prior to the article
- Step 3: previously used keywords.
- reviewing the keywords noted in the articles yielded from the keyword search noted above
- Step 1: Forward references search refers to reviewing additional articles that have cited the article
- Step 2: Forward authors search refers to reviewing what the authors have published following the article
- At the very least, the researcher must demonstrate that he or she has read the article and extracted meaningful information from it.
- Pointing at the literature vs Knowledge-level mastery
- Other research also indicates that individual and group marks should be combined in-group activities (Buchy & Quinlan, 2000; Lim et al., 2003; Romano & Nunamaker, 1998).
- > not good: reader really don’t have any idea what these references said
- Buchy and Quinlan (2000) interviewed 36 students participating in tutorial groups. These interviews indicated that the students felt they were becoming more conscious of learning processes of both themselves and their peers.
- > good: Research methodology, and references ideas.
- Han and Kamber (2001) suggest an evolution that moves from data collection and database creation, towards data management, and ultimately, data analysis and understanding.
- Not good: does not demonstrate mastery over anything beyond a set of “buzz-words”
- Han and Kamber (2001) suggest an evolution that moves from data collection and database creation, towards data management, and ultimately, data analysis and understanding. For example, data processing is a base function enabling manipulation and aggregation of data, thus facilitating searching and retrieval.
- Good: demonstrates an understanding of the concepts presented by Han and Kamber through example.
b. Research must communicate to the scientific community.
Why Conduct a Literature Review:
1. Demonstrate "what is already know?" and "what is needed to be known?"
2. Justifying the proposed study as one that contributes something new to the BoK
3. Framing the valid research methodologies, approach, goals, and research questions for the proposed study
Literature Review process:
a.Input (Collect)
b. Processing (Know > Comprehend > Apply > Analyze > Synthesize > Evaluate "quality literature" )
c. Output ("contributes something new to the overall body of knowledge")
IS Literature Review:
a. An effective IS literature search must exhaust all sources that contain IS research publications (i.e. journals, quality conferenceproceedings, etc.) that are valid to the proposed study
b. Large number of electronic and print sources are available that the novice researcher can be overwhelmed in determining quality literature.
Fitting the literature into your research:
a. Asking: "how is the work presented in the article I read related to my study?"
b. During the review of the literature researchers should utilize sources that substantiate the
presence of the problem under investigation. => enable the researcher to provide a solid argument for the need for their study
Place your study in the context of existing work
Quality research
must provide justifications for the potential contributions provided by the proposed study. =>
demonstrate how the proposed research contributes something new to the
overall BoK or advances the research field’s knowledge
B. INPUT
Where to Look for Quality IS Literature?
Quality IS research literature from leading, peer-reviewed journals should
serve as the major base of literature review as it provides sufficient theoretical background as
well as leads for additional references on the specific subject matter
Although conferences are valuable scientific venues for exchange of ideas and a major incubator for new research agendas, the overall rigor of conference proceedings is lower than one found in leading journals
=> IS researchers must ensure that references used in a proper context and with high degree
of confidence
Keywords search
Backward search
Forward search
How to Tell When You Are Done With the Literature Search?
As noted previously, the use of backward and forward literature search techniques should
provide additional valid references as the search progresses. However, it may appear to novice
researchers that this process is a never-ending one.
one common rule of thumb is that the search is near completion when one discovers that new articles only introduce familiar arguments, methodologies, findings, authors, and studies
C. PROCESSING
Know the Literature
Comprehend the Literature
Pre-comprehension level mastery vs Pre-comprehension level mastery
Cognitive/construct-level
Theory: Definition and Use in IS Literature
Constructs/variables: Definition and Use in IS Literature
Many researchers note the term “construct” similarly to the term “concept”. “a concept expresses an abstraction formed by generalization from particulars”, whereas a construct is a concept with added meaning “deliberately and consciously invented or adopted for a special scientific purpose”
Models/frameworks: Definition and Use in IS Literature
D. OUTPUTS:
Writing Arguments and Argumentation Theory
Writing the Literature Review
E. DISCUSSION:
1) Keep an annotated copy of all the articles, book chapters, or conference proceedings you read
in both hardcopy and electronic format. It is unbelievably frustrating to need to refer back to an
article and find you do not have ready access to it.
2) Highlight everything in the article that is applicable to your research, even if you don’t think
you will use the material. It is almost impossible to tell exactly what direction research will take,
and it can be very frustrating and time consuming to try to re-locate information you are almost
certain you found in a given paper.
3) Write notes to yourself about the article you are reading regarding issues, thoughts, or general
comments such as “nice methodology for …”, “interesting definition of…,” etc.
4) Write a brief (one to two paragraph(s)) annotated bibliography entry that encapsulates the essential
points applicable to your research derived from the article. It is important to note that the annotated bibliography is specific to your research and is not the same as the abstract for the article, which summarizes the entire study.
5) As one reads literature, be sure to look for and circle any terms or expressions that might serve as keywords that would facilitate the forward or backward searching described earlier.
6) Remember, it is important to place each article in the context of the body of knowledge by
identifying the applicable model(s), construct(s), theory(ies), and/or literature stream(s) (see section “Cognitive/construct-level” above). Annotate the applicable model(s), etc. on the front of the article.
Managing the literature review process
1. In defining a meaningful literature review, Levy and Ellis (2006) stated that it should "provide a firm foundation to the selection of research methodology". How can research methodology be selected through Literature Review?
2. Are there any different ways of performing literature review process except the mentioned systematic way (input-processing-output)?
3. How can researcher address all sources of related IS research publications from all literature databases and all vendors? The author provided list of ranking sources for research's input in Figure 2 and Figure 3. Are The Figure 2. ISWorld’s top 50 ranked MIS journals and electronic availability provided by Saunders (n.d.) and Figure 3. Ranked and non-ranked IS conferences with electronic availability of proceedings provided by Hardgrave and Walstrom (1997) still valid today (2015)?
Reference:
Levy, Y. and Ellis, T. J. (2006) 'A systems approach to conduct an effective literature review in support of information systems research', Informing Science: International Journal of an Emerging Transdiscipline, 9: 181-212.
Subscribe to:
Comments (Atom)